
Explore in detail how to identify, protect and minimize threats and vulnerabilities to maintain IT security. Computer threats and vulnerabilities are dangers or weaknesses that can compromise the security and proper functioning of computer systems.
Computer threats and vulnerabilities are a growing concern in today’s digital world. From computer viruses to phishing attacks, dangers lurk in every corner of the Internet. In this article, we will explore in detail how to identify, protect against, and minimize these threats to keep your systems safe and secure.
Starting at age 44, your energy, metabolism, and overall well-being may be silently declining. Don’t wait for symptoms.
- Threats: These are situations or actions that can damage, steal or alter the information stored on a computer. This may include viruses, malware, spyware, phishing, hacker attacks, among others.
- Vulnerabilities: These are weaknesses in the software, hardware or configuration of a system that can be exploited by threats to compromise security. These vulnerabilities can arise due to programming errors, lack of security updates, insecure configurations, among others.
Importance of protecting against threats and vulnerabilities
Protection against threats and vulnerabilities is crucial because:
- Protect your personal and confidential information, such as passwords, banking details, emails, etc.
- Prevent identity theft and financial fraud.
- Keeps your computer functioning properly and prevents data loss.
- Preserve the privacy and security of your online activity.
- Protect your computer from being used to carry out malicious activities without your knowledge.
Security Introduction
Your PC is under siege. Through your PC, malicious people can obtain valuable information about you and your habits. They can steal your files. Can run programs that log your keystrokes to obtain account names and passwords, credit card information, and more.
They can run software that takes up much of your computer’s processing time and use it to spam or steal from others. The threat is real and immediate. Worse yet, they may be doing these things to their customers right now. You need to protect your computer and your users’ computers from these attacks.
But what does computer security mean? Is it an antimalware program? Are they large and complex passwords? Sure, it’s both, but what about the fact that your laptop can be easily stolen or that improper ventilation can cause hard drives and other components to die?
Protecting computers requires both a solid strategy and proper tactics. For strategic reasons, it is necessary to understand the threat posed by unauthorized access to a single computer, as well as the major threats posed to networked computers.
Part of the bigger picture is knowing what policies, software, and hardware to implement to stop those threats. From a tactical perspective in the trenches, you need to master the details to know how to deploy and maintain the right tools. Not only do you need to install anti-malware programs on your users’ computers, for example, but you also need to update those programs periodically to keep up with the constant barrage of new malware.
Security, Threats and Vulnerabilities
Threats to your data and PC come from two directions: accidents and malicious people. All kinds of things can go wrong with your computer, from users gaining access to folders they shouldn’t see to a virus attacking and deleting folders. Files can be deleted, renamed, or simply lost. Hard drives can fail and optical discs become scratched and unreadable. Accidents happen and even well-intentioned people can make mistakes.
Threats need some way to access a network or facility, whether accidental or malicious, internal or external, and that’s where vulnerabilities come in. A vulnerability is a weak point in your defenses that allows a threat to cause damage.
Vulnerabilities may exist in an organization’s physical security or in its networks. Understanding the different types of vulnerabilities and the threats that will attempt to exploit them is vital to protecting your organization’s data, reputation, and security. Threats take advantage of vulnerabilities to cause harm.
Security Threats
Unfortunately, many people intend to harm you. Combine that intent with a talent for computers and you have a dangerous combination. Let’s look at some of those risks:
Malicious Entities
In some cases, the threat in question is an individual, also known as a threat actor. Whether it’s an external malicious actor like a hacker or an internal malicious actor like a disgruntled employee, threat actors need some way to use vulnerabilities to their advantage.
A threat actor identifies one or more vulnerabilities in a network or physical security system, uses some combination of attacks to exploit the vulnerability or vulnerabilities, and proceeds to carry out their nefarious plans. Very rarely will a malicious actor use just one method. For example, a malicious actor attacking from outside the organization may employ a phishing scam ().
Zero-Day Attack
A zero-day attack is an attack on a vulnerability that software developers were not yet aware of. It gets its name because the developer of the defective software has not had days to fix the vulnerability.
Phishing
Phishing attacks are fraudulent emails, text messages, phone calls, or websites designed to trick users into downloading malware, sharing sensitive information, or personal data (for example, social security numbers, credit cards, bank accounts or login credentials) or other actions that expose themselves or their organizations to cybercrime.
Successful phishing attacks frequently lead to identity theft, credit card fraud, ransomware attacks, data breaches, and large financial losses for individuals and corporations.
Phishing is the practice of tricking, pressuring, or manipulating people into sending information or assets to the wrong people.
Generally, phishing is not so much a threat as a tool to carry out threats, for example if you use my email address to impersonate me and ask my employees to submit their usernames and passwords to log in to the grid.
Path Attack
In a path attack, an attacker exploits communications between two systems, covertly intercepts traffic believed to be only between those systems, reads or in some cases even changes the data, and then sends it. A classic en-route attack would be someone using special software on a wireless network to make all clients think your laptop is a wireless access point. It could then listen to that wireless network, collect all conversations, and gain access to passwords, shared keys, or other sensitive information.
Session Hijacking
Somewhat similar to in-path attacks, session hijacking attempts to intercept a valid computer session to obtain authentication information. Unlike path attacks, session hijacking only attempts to obtain authentication information, not necessarily eavesdropping as in a path attack.
Brute Force Attack
Brute force is a method used by threat actors in which they guess many or all possible values for some data. Most often the term brute force refers to an attempt to crack a password, but the concept also applies to other attacks. You can brute force search for open ports, network IDs, usernames, etc. Virtually any attempt to guess the contents of some type of data field that is not obvious (or hidden) is considered a brute force attack.
There are two other tools that attackers use to brute force passwords: dictionaries and rainbow tables. A dictionary attack is a form of brute force attack that essentially guesses every word in a dictionary. A dictionary used to attack passwords could contain all the passwords leaked online.
A terrible way to authenticate users is to save a copy of their password in a database and verify it every time they log in. Hackers love to steal these databases because they can test the username and password on popular services and use the passwords to improve the dictionaries they use to guess passwords.
Rainbow tables use complicated mathematics to condense hashed dictionary tables. entrances dramatically. They are binary files, not text files, and can store staggering amounts of information in a relatively small size.
Denial of Service
A denial of service (DoS) attack uses various methods to overwhelm a system, such as a web server, and render it essentially non-functional. DoS attacks were relatively common in the early days of the Web. Nowadays you will see distributed denial of service (DDoS) attacks that use many machines simultaneously to attack a system.
A DDoS attack is typically executed through a botnet. A botnet consists of a large number of systems infected with malware designed to allow an attacker to control them and use them to send disruptive traffic designed to disable a resource.
SQL Injection
Chances are you’ve already deduced that accessing, stealing, and destroying data are common goals of malicious actors, so let’s take a look at one of the favorite methods hackers use to achieve them. SQL is an acronym for Structured Query Language. SQL is a language that allows a program to interact with a database using various commands and queries.
A SQL injection occurs when an attacker enters SQL commands into an input field as you would see in a web application, to gain access to data in a database that they should not be able to see. You won’t need to know the ins and outs of how SQL injection is performed, but know that preventing it is done at the programming level, with something known as input validation.
Unauthorized Access
Unauthorized access occurs when a person accesses resources (data, applications, and hardware) without permission. “Resources” in this case means data, applications and hardware. A user can alter or delete data; access sensitive information, such as financial data, personal files or emails; or use a computer for purposes not intended by the owner.
Not all unauthorized access is malicious; Often, this problem arises when users snooping around a computer out of curiosity or boredom discover that they can access resources in a way that the primary user didn’t have in mind. Unauthorized access becomes malicious when people knowingly and intentionally exploit weaknesses in your security to obtain information, use resources, or destroy data.
One way to gain unauthorized access is intrusion. You could imagine someone breaking down a door and hacking into a computer, but most of the time it’s someone sitting in front of their home computer, trying various passwords over the Internet. It’s not as glamorous, but it will do. Another insidious method is to manipulate people into providing privileged information or access that would not otherwise be available to a potential attacker.
Psychological Manipulation
Although you are more likely to lose data due to accidents, the acts of malicious users grab the headlines. Most of these attacks (misnamed social engineering) are the result of an entire process of using or manipulating people within organizations to gain access to their network or facilities and cover the many ways in which humans can use others to gain access. unauthorized information.
It relies on attackers’ ability to understand human behavior, exploit trust, and manipulate people’s emotions.
This information can be a network login, a credit card number, company customer data, almost anything you can imagine that a person or organization does not want outsiders to access.
Infiltration
Hackers can use phishing to enter your building physically disguised as cleaning staff, repair technicians, couriers, etc. They then snoop through desks looking for anything they can find.
They could talk to people within the organization, collecting names, office numbers, department names – small things in themselves, but powerful tools when later combined with other social engineering attacks.
Disguising yourself as a legitimate user (with a fake badge and all) allows malicious people to gain access to locations and therefore potentially your data.
Dumpster diving
Is the generic term for searching for information in trash. This is also a form of intrusion. The amount of confidential information that ends up in any organization’s trash can staggers the mind. Years ago, I worked with an IT security guru who gave me and other IT people a tour of our office junk.
In a 20-minute tour of one office’s personal trash cans, we gained enough information to easily access the Internet, as well as seriously embarrass more than a few people. When it comes to information, the trash is the place to look.
Shoulder browsing is another technique for gathering information and gaining unauthorized access. Shoulder browsing is simply looking at someone’s screen or keyboard to obtain information, often passwords. As the name implies, it usually requires the bad guy to look over his shoulder to see what he’s doing.
Vishing
Vishing is one of the most common attacks. In this case, the attacker makes a phone call to someone in the organization to scam them and obtain information. The attacker attempts to impersonate someone within the organization and uses this to obtain the desired information. Probably the most famous of these scams is: I forgot my username and password.
In this tactic, the attacker first learns the account name of a legitimate person in the organization, usually using the infiltration method. The attacker then calls someone in the organization, usually the help desk, in an attempt to collect information, in this case a password.
Vishing is certainly not limited to attempts to gain network access. There are documented vishing attacks against organizations aimed at obtaining cash, blackmail material or other valuables.
Phishing
Phishing is the act of attempting to get people to provide their usernames, passwords, or other security information by impersonating another person electronically. A classic example is when a bad guy sends you an email that’s supposed to come from your local credit card company asking you to send him your username and password. Phishing is by far the most common form of psychological manipulation carried out today.
Phishing refers to a fairly random act of evil. The attacker targets anyone naïve enough to take the bait. Spear phishing is the term used for targeted attacks, like when a bad guy goes after a specific celebrity.
The dangerous thing about phishing is that the bait can be carefully tailored using details from the target’s life. A particularly dangerous form of phishing specifically targets people who hold high positions in an organization, such as executives or administrators. This is known as whaling.
Evil Twin
One of the reasons breaches can be so dangerous is that a malicious actor can place devices within an organization’s network. A particularly dangerous example of this is known as the evil twin. An evil twin is a fake wireless access point configured to mimic the characteristics of a legitimate device and network, in order to lure unsuspecting users into connecting to the attacker’s device. By doing this, the attacker can spy on Internet traffic, steal user credentials, and use this information to cause additional damage.
Internal threats
Threats to your network or facility don’t just come from the outside. Sometimes the threat exists within the organization itself. This is known as an insider threat. An insider threat is any security risk that originates from an individual within an organization. Sometimes the insider in question is malicious and seeking to steal funds or information. It may also be a disgruntled current or former employee seeking revenge on the company.
However, don’t make the mistake of thinking that all insider threats are malicious: sometimes accidents happen and the insider threat is a well-intentioned person simply trying to make your or someone else’s job easier. The real threat here is access to the systems and facilities they have and what they can do with them.
There are several ways to mitigate insider threat risks, most of which focus on access control. Only giving users access to what they need to do their jobs and removing relevant user and administrator accounts when someone leaves the company are examples of insider threat mitigation.
Data Destruction
Data destruction, which is often an extension of unauthorized access, means more than simply deleting or corrupting data intentionally or accidentally. It’s easy to imagine some evil hacker accessing your network and deleting all your important files, but authorized users can also access certain data and then use it beyond what they are authorized to do.
A good example is the person who legitimately accesses a Microsoft Access product database to modify product descriptions, only to discover that he can also change product prices.
This type of threat is particularly dangerous when users are not clearly informed about the extent to which they are authorized to make changes. An authorized user can make modifications to data when requested, they can answer: “If they didn’t allow me to change it, the system wouldn’t let me do it.”
Many users believe that the systems are configured in a way that would not allow them to do anything inappropriate, as if the computers knew ethics or had intelligence. Even Artificial Intelligence, which is currently so fashionable, has absolutely no Intelligence, no Ethics, no Feelings, it is nothing more than a large Database that answers your questions or the inputs of a process and gives the answers according to the entries or the information stored in that database, that’s all, nothing more!
Administrative Access
Each operating system allows you to create user accounts and give those accounts a certain level of access to files and folders on that computer. As an administrator, supervisor, or root user, you have complete control over almost every aspect of the computer.
This increased control means that these accounts can cause much more damage when compromised, amplifying the danger of other threats. The idea is to minimize both the number of accounts with full control and the time they spend connected.
Even if a user absolutely needs this access, uses strong passwords, and practices good physical security, malware installed through a convincing phishing attack could exploit that control to access files, install software, and change settings that a typical account couldn’t touch.
System Crash/Hardware Failure
As with any technology, computers can and will fail, usually when you least expect it. Hard drives fail, power goes out, etc. You need to create redundancy in failure-prone areas (such as installing backup power in case of a power failure) and make those all-important data backups.
A specific security example would be having redundant firewalls to protect the network in case one of them fails.
Security Physical Theft
Never forget that the best network software security measures can be useless if you don’t physically protect your systems.
Malware (Malicious Software)
Networks are undoubtedly the fastest and most efficient vehicles for transferring computer viruses between systems. The news focuses on numerous malware attacks coming from the Internet, but a large number of these attacks still come from users inserting programs onto optical discs and USB drives.
Spam
All of us who have an email address have seen spam at some point in our lives. Spam is the digital equivalent of junk mail; It is a mass email that is sent to as many people as possible in the hope that at least some of them will interact with it. Sometimes spam is just a nuisance, but it can also be a threat to your network. Phishing attempts, malicious links, and attachments containing malware are just some of the dangers that spam can present.
In the United States of America, the Federal Communications Commission has adopted rules to protect consumers and businesses from unwanted email messages on wireless devices such as mobile phones. The Commission initiated this rulemaking process as mandated by Congress in the Non-Solicited Pornography and Marketing Assault Control Act of 2003 (CAN-SPAM Act).
Congress passed the CAN-SPAM Act to address the problem of unwanted commercial email messages. The CAN-SPAM Act requires the Federal Communications Commission to issue rules regarding commercial email and some text messages sent to wireless devices such as cell phones, not email in general. Specifically, Section 14 of the CAN-SPAM Act requires the Commission to develop rules to protect consumers from “unwanted commercial messages from mobile services.”
Security Vulnerabilities
Threats to your computers and facilities can be terrifying, but they need some way to gain access before they can cause problems. Threats compromise a system by exploiting vulnerabilities in a computer, network, company policy, or physical security to gain access.
Once a vulnerability is exploited, whether by an outside hacker, a disgruntled employee, or even inadvertently by a well-intentioned person simply trying to make their job easier, chaos can ensue. If vulnerabilities are not identified and addressed, data deletion, data theft, extortion, and all sorts of other nasty things can occur.
Have you ever been working on your computer, gaming, or having a Zoom meeting and suddenly your operating system asks you to install updates that require a restart? Most likely yes, and as disturbing as this may be, the disruptions that could result from ignoring these messages are even worse.
Operating Systems Patches
This is because these warnings tell you to patch your operating system, and often those patches are intended to address a security risk. Unpatched systems are vulnerable to a growing list of vulnerabilities that attackers know about and are actively exploiting.
Leaving a system unpatched is like leaving a second-story window open while you go on vacation. Sure, you may come home and see that everything is fine, but you may also have been robbed blind.
If leaving your systems unpatched is like leaving a second-story window open when you go on vacation, an unprotected system is like leaving your front door open with a sign on the lawn inviting people in. An unprotected system lacks key security tools such as anti-malware software and firewalls.
Without this, there is nothing stopping a hacker from doing whatever they want on your network. They can send malware, attempt to connect directly to your internal network, and attempt to steal or destroy your sensitive information, and do all this with a relatively low chance of being detected. An unprotected system is a serious vulnerability, whether at home, a small business, or a large corporation. If you must have unprotected systems, be sure to isolate and monitor them.
Operating Systems End Of Life
Operating systems also have a useful life. Over time, as new and sometimes improved operating systems are released, older ones disappear. Once an old operating system is completely removed, it stops receiving security updates as new vulnerabilities are discovered.
These operating systems are known as end-of-life (EOL) operating systems and can present a significant vulnerability to a network if even one device is still using an EOL operating system. It is a fairly common problem, because operating system updates can be expensive and disruptive to a company’s operations.
Still, ensuring that operating systems are well supported and continue to receive regular security updates is an important way to mitigate vulnerabilities.
In the best of all possible worlds, your organization will use a combination of policies, systems, and effort to ensure that devices on your networks never have vulnerabilities like these. But in reality, a system may need to postpone updates for a long time for various reasons.
Users may need time to comply or need network access to do so. The accounting department may need software that only works on an EOL operating system, etc.
Security Concepts and Technologies
Once you’ve assessed the threats to your computers and networks, you need to take steps to protect those valuable resources. Depending on the complexity of your organization, this may be a small job covering some basic security concepts and procedures, or it may be extremely complex.
Controlling access is the key. If you can control access to data, programs, and other computer resources, you have protected your systems. Access control is made up of interconnected areas of physical and logical security that a good security-minded technology should think about: physical security, authentication, users and groups, and security policies.
The first step is to understand physical security, which includes methods to prevent physical access to facilities, systems, and information, and the second is to understand logical security to learn how to protect your network, authenticate users, and employ effective security policies.
Physical Security
For most people, when they hear the word security, the first thing they think of is things like guards, fences, security cameras, and the like. That’s because they’re thinking about physical security.
Physical security is often an organization’s first line of defense. It includes fences and gates that keep people off the property, locks that prevent people from entering a building or area they should not enter, and guards that use surveillance tools and alerts to keep an eye on things.
Physical security involves defending facilities and systems from physical threats, both internal and external. There are layers of physical security that can and often do overlap with logical security tools to provide effective security coverage.
Securing Facilities
The first order of security is to limit access to your physical hardware. The security market is huge, but the options basically boil down to fences, gates, locks, alarms, and keeping a close eye on things. The first step is to understand that all of these pieces can fail or be destroyed. Great security involves organizing and layering many pieces so that they can enhance each other’s strengths and compensate for their weaknesses.
Think about the access control lobby. A low-tech solution like a traditional door lock is just an obstacle for someone with a lockpick and a moment alone with the lock. Access control lobbies are great because they combine simple measures like doors, locks, security guards, and an entry checklist in a way that is much harder to overcome than one or two locked doors.
Some facilities can further improve the security of their entrance by adding a metal detector. As we already mentioned, threats originate both inside and outside the organization. A metal detector is a good way to help prevent people from bringing in dangerous objects that they could use to cause harm and from leaving with something that doesn’t belong to them.
Sometimes it is necessary to extend access control beyond the door to the property boundary. Many facilities have more than one entrance or multiple buildings. As a result, organizations can add an additional line of defense to keep unauthorized persons off company property.
Fences are often used to stop people from snooping where they shouldn’t. Bollards, those short concrete or metal posts sometimes seen in areas with a lot of foot traffic, can be used to prevent vehicles from getting too close for convenience.

Enhancing Security Measures: Tools and Access Control Options
Security guards are great, but they can’t be everywhere at the same time. They need some way to keep an eye on things. That’s where the following tools come into play:
- Security personnel can use video surveillance to monitor facilities from a centralized location.
- Good lighting makes it more difficult for a potential wrongdoer to avoid detection, with the added benefit of decreasing the likelihood of workplace accidents for staff.
- Motion sensors can be used to inform you if something or someone is detected so you can take a closer look.
- Alarm systems can serve a variety of functions, from warning the IT department of an attempted network breach to informing staff of a security issue or alerting security personnel or authorities if a theft occurs outside Of schedule.
Any combination of these tools is a great addition to a solid security plan, but it’s also important to ensure that people within the organization don’t have access to things they shouldn’t have. This brings us to the next set of access control options.
Traditional door locks aren’t terrible, but the keys are easy to copy and the cost of changing locks frequently adds up quickly. An organization ready to go beyond the basics can adopt a keyless locking system powered by employee ID cards, especially those with authentication tools such as radio frequency identification (RFID) or smart cards to control building access. and/or to the rooms.

Locking systems
Once an attacker has physical access to the building, protecting your hardware becomes much more difficult. There are a few options here, but don’t plan on them doing much more than slowing someone down for a few minutes:
- Equipment locks can prevent someone from leaving quickly with hardware.
- USB locks make it more difficult to plug in a USB drive to load malware to steal data.
- RJ45 locks limit an intruder’s ability to gain access to the wired network.
- Server locks limit access to ports and drives on a server. There are also lockable rack doors to limit access to the front or back of an entire server rack.
These devices are meaningless if an intruder can walk in like he belongs, sit down in front of an unattended, connected computer, and get to work. Do not leave a logged-in PC unattended, even if it is just a standard or guest user.
If you must step away for a moment, manually lock the computer (or screen) with a hotkey or the operating system’s main menu. On a Windows system, simply press WINDOWS-L on the keyboard to lock it.
If you’re in charge of security best practices for multiple users, using screen saver locks (configured to show the login screen on resume) can be a big help for users who might forget to lock their systems when They take a break or go to lunch. Both Windows and macOS allow you to go a step further and set an automatic timeout and screen lock, where the screen goes blank after a few minutes and a password is required to log in.
Security Confidential Information
Locking down unattended systems is a great habit, but it won’t help much if the intruder can see the user enter their password or can read it on a sticky note on the monitor. Do not write down passwords and leave them visible. Teach users to follow strong password guidelines. Be aware of the risk of shoulder surfing. Ideally, the office layout should make it impossible for anyone to observe the user without them noticing.
If users need to work with sensitive information anywhere where someone unauthorized can see the screen, they may need a privacy filter (also called a privacy screen): a framed sheet or film that is applied to the front of their monitor. Privacy filters reduce the viewing angle, making it impossible to see the screen unless you are directly in front of it. Store paper copies of critical, personal or confidential documents out of sight and destroy any you don’t need immediately.

Logical Security
While physical security focuses on preventing unauthorized access to facilities and equipment, logical security focuses primarily on denying access to computers and data. Logical and physical security features are usually combined for maximum effectiveness. In some cases, such as biometrics, the security tool can be used for both logical and physical security applications.
Logical security refers to the measures and practices implemented to protect computer systems, networks and data from unauthorized access, alteration or destruction through logical or software means. It encompasses various technologies, policies and procedures designed to safeguard digital assets and ensure the confidentiality, integrity and availability of information.
Below is a breakdown of logical security and how it can be implemented:
Access Control
Access control mechanisms regulate who can access what resources within a system or network. This includes user authentication (e.g., passwords, biometrics, smart cards), authorization (defining user privileges and permissions), and accountability (logging and auditing access activities).
Encryption
Encryption is the process of converting data into a format that can only be read or processed after decryption with the correct key. It is used to protect the confidentiality of data during storage, transmission and processing. Techniques such as symmetric encryption (using the same key for encryption and decryption) and asymmetric encryption (using public and private keys) are commonly used.
Firewalls
Firewalls are network security devices that monitor and control incoming and outgoing network traffic based on predetermined security rules. They act as a barrier between trusted internal networks and untrusted external networks (such as the Internet) to prevent unauthorized access and mitigate various network-based attacks.
Intrusion Detection and Prevention Systems (IDPS)
IDPS are security solutions that monitor network or system activities for malicious activity or policy violations. They detect and respond to suspicious behavior, including known attack signatures, anomalies, and policy violations. IDPS can operate in passive mode (detecting and recording incidents) or active mode (blocking or mitigating detected threats).
Patch Management
Patch management involves identifying, acquiring, testing, and applying patches (software updates or fixes) to address vulnerabilities in operating systems, applications, and firmware. Regular patching helps mitigate security risks associated with known vulnerabilities and ensures systems are up-to-date with the latest security improvements.
Security Information and Event Management (SIEM)
SIEM solutions collect, analyze, and correlate security event data from various sources across an organization’s IT infrastructure. They provide real-time visibility into security events, threat detection, incident response, and compliance reporting. SIEM helps organizations proactively identify and respond to security threats and policy violations.
User Awareness and Training
Human factors play a critical role in logical security. Employees should receive regular training on security best practices, such as password management, phishing awareness, data handling procedures, and incident reporting. Promoting a security-conscious culture helps mitigate the risk of social engineering attacks and insider threats.
Implementing logical security involves a holistic approach that addresses the technical, procedural, and human aspects of security. Organizations must conduct risk assessments, develop security policies and procedures, implement appropriate security technologies, and continually monitor and improve their security posture to effectively protect against evolving threats. Collaboration between IT security teams, management, and end users is essential to the successful implementation and maintenance of logical security measures.
Security Policies
Although permissions control how users access shared resources, there are other functions that you must control that are outside the scope of resources. For example, do you want users to be able to access a command prompt on their Windows system? Do you want users to be able to install software? Would you like to control which systems a user can log in to or what time of day a user can log in?
All network operating systems give you some ability to control these and literally hundreds of other security parameters, under what Windows calls policies. Policies are like permissions for activities, unlike true permissions, which control access to resources.
Local Policies
Typically, a policy applies to a user account, a computer, or a group. Let’s use the example of a network composed of Windows systems with a Windows server. Each Windows client has its own local policy program, which allows you to place policies only on that system.
There is a tool used to set local policies on an individual system, called Local Security Policy, which is used to deny the Guest account the ability to log in locally.
Local policies work great for individual systems, but can be difficult to configure if you want to apply the same settings to more than one PC on your network. If you want to apply policy settings in bulk, you must update domain-based Windows Active Directory features.
Group Policies
You can use organizational units (OUs) that organize users and devices logically in a folder-like hierarchy; then exert deity-like control (Microsoft prefers the term granular) to apply a different group policy to network clients on each drive.
One important thing to note about Active Directory group policies is that they override local policies. For example, if you have a local policy that allows a specific user to install third-party software and then set a group policy for the domain that prevents all users from doing so, the user will not be able to install the software.
Do you want to set the default wallpaper for each PC in your domain? Group policy can do that. Do you want to make certain tools inaccessible to everyone except authorized users? Group policy can do that too.
Do you want to control Internet access, redirect home folders, run scripts, deploy software, or simply remind people that unauthorized network access will get them nowhere fast? Group policy is the answer.
This is just a simple example of the settings you can configure using Group Policy. You can apply literally hundreds of settings through Group Policy, from the largest to the smallest, but don’t worry too much about familiarizing yourself with each and every one of them.
Essential Group Policy Settings
Group policy configuration is an important topic in most Microsoft certification paths. Although we could never list all the possible policies you can enable on a Windows system, here is a list of some of the most used ones:
- Prevent registry edits If you try to edit the registry, you will receive an error message.
- Prevent access to the command prompt Prevent users from accessing the command prompt by disabling the Run command and the command prompt shortcut.
- Log in locally Defines who can log in to the system locally.
- Shut down the system Defines who can shut down the system.
- Minimum password length Forces a minimum password length.
- Account Lockout Threshold Sets the maximum number of login attempts a person can make before being locked out of the account.
- Disable Windows Installer Prevents users from installing software.
- Printer Scanning Allows users to search for printers on the network, instead of just using assigned printers.
Account management security policy best practices dictate that you should implement restrictive user permissions, login time restrictions, lock out accounts based on failed attempts, disable guest accounts, and disable built-in autorun features or automatic playback of the operating system. Finally, you should always change the system’s default usernames and passwords when possible.
Network Security
Networks are also threatened from outside such as attacks through the Internet, firewalls and wireless networks.
Malicious Software
The wonderful thing about the Internet is the ease of accessing resources anywhere in the world, all from the comfort of wherever you are. This connection, however, works both ways and people from all over the world can potentially access your computer from the comfort of their evil lairs. The Internet is flooded with malicious software.
The term malware defines any program or code designed to do something to a system or network that you do not want done. Malware comes in a wide variety of forms, including viruses, worms, ransomware, spyware, Trojan horses, keystroke loggers, cryptojacking, and rootkits.
Malware has been pestering PC users since the 1980s and has evolved into many forms over the years. From the classic boot sector viruses of the ’90s to the more recent threats of ransomware and attacks on critical infrastructure, malware is an ever-changing threat to your users and data.
A virus is one of the most common forms of malware and is a program that has two functions: replicate and activate. Replication means that it makes copies of itself, injecting itself as extra code added to the end of executable programs or hiding in the boot sector of a drive.
Boot sector viruses can be particularly nasty because they live inside your system’s boot partition and activate their malicious code before security software can start and prevent it. Activation occurs when a virus does something like corrupt data or steal private information. A virus only replicates on other drives, such as USB sticks or optical media. It does not self-replicate between networks. A virus needs human action to spread.
Malware Signs and Symptoms
If your PC has been infected by malware, you will encounter some strange things before you can even run an anti-malware scan. Like a medical condition, malware causes unusual symptoms that should stand out in everyday computer use.
Malware’s greatest strength is its flexibility: it can look like anything. In fact, many malware attacks may look like normal PC “working”: momentary slowdowns, one-time random crashes, etc. Knowing when a strange app crash is actually a malware attack is half the battle.
Slow performance on a PC may mean that you are running too many applications at once or that you have received malware. Apps can crash randomly, even if you don’t have too many loaded. How do you tell the difference? In this case, it is the frequency. If this happens frequently, even when all your apps are closed, you have a problem. This also applies to frequent crashes, whether PC-based or OS-based crashes. If Windows starts misbehaving (more than usual), run your anti-malware application immediately.
However, malware does not always come to light with major system failures. Some malicious programs try to rename system files, change file permissions, or hide files completely. You may start receiving emails from colleagues or friends questioning a message “you” sent them that looked like spam.
You may receive automated responses from unknown sent emails that you know you didn’t send. An increase in desktop alerts that don’t appear to have a legitimate cause or unwanted notifications within the operating system can also be signs that it’s time to look for malware. You may even receive fake alerts about your computer’s antivirus protection. Most of these issues are easily detected by a regular anti-malware scan, so as long as you stay vigilant, you should be fine.
Malware Prevention and Recovery
The only way to permanently protect your PC from malware would be to disconnect it from the Internet and never allow any potentially infected software to touch your precious computer. Since neither situation is possible today, it is necessary to use specialized anti-malware programs to help prevent inevitable attacks.
Even with the best antimalware tools, there are times when malware manages to attack your computer. When you discover infected systems, you need to know how to stop the spread of malware to other computers, how to repair infected computers, and how to remediate (restore) the system as close to its original state as possible.
Deal with malware
You can deal with malware in several ways: anti-malware programs, training and awareness, patch/update management, and remediation.
At a minimum, every computer should be running an anti-malware program. If possible, add a device that runs anti-malware programs against incoming data on your network. Also remember that an antimalware program is only as good as its updates. Users should be trained to look for suspicious ads, programs and pop-ups, and understand not to click on them.
The more you teach users about malware, the more aware they will be of potential threats. Your organization should have policies and procedures so everyone knows what to do if they encounter malware. Finally, a good technician maintains proper incident response logs to see if any attack patterns emerge. He or she can then adjust policies and procedures to mitigate these attacks.
One of the most important malware mitigation procedures is to keep the systems under your control patched and up-to-date through proper patch management. Microsoft, Apple, and Linux maintainers do a very good job of releasing bug fixes and patches as soon as problems arise. If your systems are not configured to update automatically, perform manual updates regularly.
Anti-Malware Programs
An antimalware program, like a classic antivirus program, protects your PC in two ways. It can be either sword or shield, functioning in active search and destroy mode and passive sentry mode. When commanded to search and destroy, the program scans the computer’s boot sector and files for viruses and, if it finds any, presents you with available options to remove or disable them.
Antivirus programs can also function as antivirus shields that passively monitor a computer’s activity, checking for viruses only when certain events occur, such as the execution of a program or the download of a file.
The term antivirus (and antispyware or anti-anything) is becoming obsolete. Viruses are only a small component of the many types of malware. Many people still use the term synonymously with antimalware.
Antivirus programs use different techniques to combat different types of viruses. They detect boot sector viruses by simply comparing the drive’s boot sector with a standard boot sector. This works because most boot sectors are basically the same.
Some antivirus programs back up the boot sector. If they detect a virus, programs use that backup to replace the infected boot sector. Executable viruses are a little harder to find because they can be in any file on your disk.
To detect executable viruses, the antivirus program uses a signature library. A signature is the code pattern of a known virus. The antivirus program compares an executable file with its signature library. There have been cases where a perfectly clean program just happened to contain a virus signature. Typically, the creator of the antivirus program provides a patch to prevent further alarms.
Windows Defender
Windows comes with Windows Defender (simply called Virus & Threat Protection in Windows 10/11), a great tool for detecting most malware, but it’s not perfect. You can also complement Windows Defender with a second malware removal program.
These apps work exactly as advertised. They detect and remove malware of all types: hidden files and folders, cookies, Registry keys and values, you name it. There is an Anti-Malware called Malwarebytes and it is free for personal use, https://www.malwarebytes.com.
User Education on Common Threats
A powerful tool to prevent malware attacks and reduce their impact when they occur is to educate end users. Teach users to be wary of incoming emails they don’t clearly recognize and to never click on an attachment or URL in an email unless they are 100 percent sure of the source.
With ransomware attacks increasing over time, good anti-phishing training has become an absolutely essential tool in the IT security toolbox.
Anti-phishing training involves teaching users how to recognize and critically examine incoming emails to avoid falling victim to attempts by this threat. Anti-phishing training has benefits that extend beyond organizational boundaries, as these types of attacks also occur in SOHO environments. Regardless of where or why a person is using their device, this is very useful education.
Explain the dangers of visiting questionable websites to your users and teach them how to react when they see questionable actions being taken. All web browsers have built-in attack site warnings like the one below:
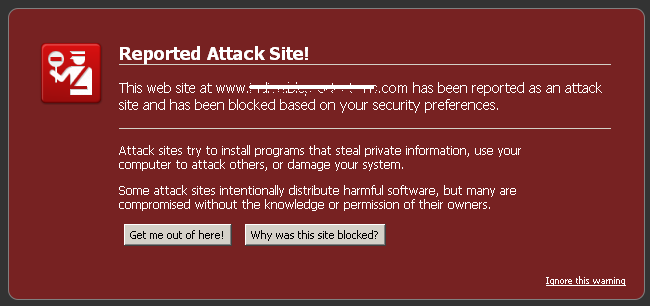
Nobody wants their systems infected with malware. Users are motivated and happy when you give them the skills necessary to protect themselves. The bottom line is that educated and aware users will make your life a lot easier.
Malware Prevention Tips
The secret to preventing damage from a malware attack is to prevent malware from reaching your system in the first place. One way to do this is with a variation of traditional DNS: secure DNS. Secure DNS can describe a remote DNS provider or software that implements some additional filters to prevent your devices from visiting all kinds of malicious websites.
If you can’t prevent malware from reaching your system, a good next step is to catch it when it comes in the door. All good antivirus/antimalware programs (like the built-in Windows Defender antivirus) include an antivirus shield that automatically scans email, downloads, running programs, etc.

Use your antivirus shield. It is also a good idea to scan PCs daily for possible virus attacks. Last but not least, know the source of any software before uploading it. Only install apps from trusted sources, such as the manufacturer’s website or well-known app stores. Avoid untrusted software sources at all costs, such as free registry cleaners from some supporting domain.
Keep your antivirus and antimalware programs (including Defender Antivirus) up to date. New viruses and other malware appear daily, and your programs need to stay on top of them. The list of virus signatures that your antivirus program can recognize, for example, is called a definition file, and updated definitions play a critical role in keeping the latest malware off your system.
Fortunately, most antivirus programs update automatically. Additionally, you should periodically update the core programming of the anti-malware software (called the engine) to employ the latest improvements that the developers have included.
Bootable Media Anti-Malware Tools
If you run antimalware software and your computer still gets infected, especially after rebooting, you need a more serious antimalware tool. Many antimalware companies provide a bootable optical disk or USB flash drive (or show you how to create one) that allows you to boot from a clean operating system and run the same antimalware software, but this time not corrupted by malware on your system.
Tips for Recovery After a Malware Attack
When the inevitable happens and your or another user’s computer becomes infected with malware, such as a computer virus, you need to take certain steps to prevent the problem from spreading, and get your computer back up and running safely. Below we show a procedure with best practices for malware removal:
- Investigate and check malware symptoms.
- Quarantine infected systems.
- Disable System Restore in Windows.
- Repair infected systems and Update anti-malware software.
- Schedule scans and run updates.
- Enable System Restore and create a restore point in Windows.
- Educate the end user.
Reinstalling Operating System
In addition to this malware removal process, reinstalling the operating system as another way to ensure your system is malware-free: simply restore a full system backup or Reinstall Windows (what we call a clean copy), of course, making sure before you back up everything on your mass storage drive(s) (on Windows, you can make or restore one with the Backup and Restore Utility).
You should have space to store one or more full backups, plan far enough in advance to have one or more recent backups available, know that at least one is malware-free, and be prepared to back up files/files. user data separately. You won’t always have this option, but a good way to start is to back up user files and data separately and perform a full system backup once you have all the software you need installed and configured.
If you try to reinstall your operating system from a backup and discover that your system is still infected, it may be time to try as we already mentioned what is known as a Clean Installation, which means simply starting from a fresh copy of Windows and treat it as if it were new device. This also has disadvantages as it means starting from scratch with your system’s apps and data. In some cases, this may be your only option, but it is not always ideal.
Recognize and Quarantine
The first step is to identify and recognize that a potential malware outbreak has occurred. If you are monitoring network traffic and a computer starts sending emails, it is a good indicator of malware. Or users might complain that a computer that ran quickly the day before seems too slow.
Many networks employ software such as open source PacketFence that automatically monitors network traffic and can disconnect a machine from the network if that machine begins sending suspicious packets. You can also quarantine a computer manually by unplugging the network cable. Once you are sure that the machine is not capable of infecting others, you are ready to find the virus or other malware and get rid of it.
At this point, you need to disable System Restore. If you make any changes in the future, you do not want the virus to be included in any saved restore points. To disable System Restore in Windows, open Control Panel and then the System applet. Click the System Protection link to open the System Properties window with the System Protection tab displayed. In the Protection Settings section, select a drive and click Configure. In the System Protection dialog box that opens, select Turn off system protection. Repeat the procedure for each hard drive in the system.
Search and destroy
Once you have isolated the infected computer (or computers), you should access a secure boot environment and run anti-malware software. You can try Windows Recovery Environment on Windows 10/11, because it requires nothing more than a reboot. If that doesn’t work, or you suspect a virus is in the boot sector, you should turn to an external boot source, such as a bootable optical disk or USB flash drive.
Get in the habit of having an anti-malware flash drive or bootable optical media on hand. If you suspect a virus or other malware, use the bootable media, even if your anti-malware program claims to have eliminated the problem. Shut down the PC and reboot it from the anti-malware disk or flash drive (you may need to change the CMOS settings to boot from optical or USB media).
Once you reach a bootable environment, update your anti-malware software and then run the more comprehensive scan. Then check all removable media that were exposed to the system and any other machines that may have received data from the system or are networked to the clean machine. A virus or other malicious program can often lie dormant for months before anyone becomes aware of its presence.
Email remains a common source of viruses and opening infected emails is a common way to become infected. Viewing an email in a preview window opens the email message and exposes your computer to some viruses. Download files only from sites you know are safe and avoid less reputable corners of the Internet, the most likely places to get computer infections.
Remediate
Malware infections can cause a lot of damage to a system, especially to sensitive files needed to load Windows, so you may need to remediate previously infected systems after cleaning the drive or drives. Remediation simply means fixing the things that the virus or other malware damaged. This may mean replacing corrupt Windows Registry files or even startup files.
If you cannot start Windows after the malware scan is completed, you must boot to the Windows preinstallation environment and use the Windows Recovery Environment/System Recovery Options.
With Windows Recovery Environment, you have access to more repair tools such as Startup Repair, System Restore, System Image Recovery, Update, and Command Prompt. Run the appropriate option for the situation and you should have your computer repaired properly in no time.
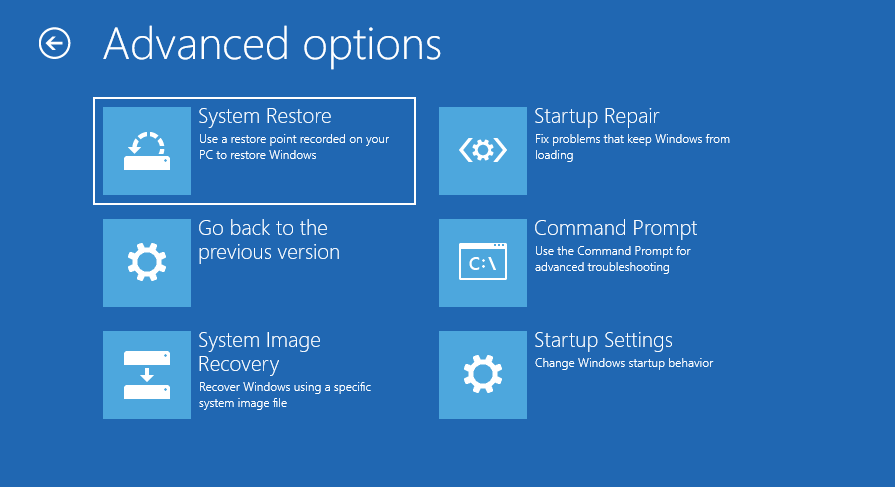
Remember to re-enable System Restore and create a new restore point once the system has been repaired.
Educate End Users
The best way to avoid having to deal with malware is education. It’s your job as an IT person to talk to your users, especially those whose systems you just spent an hour removing nasties, about how to avoid these programs.
Show them examples of dangerous emails they should not open, websites they should avoid, and the types of programs they should not install or use on the network. Any user who understands the risks of questionable actions on their computers will usually do the right thing and stay away from malware.
Finally, have your users run antivirus and antispyware programs regularly. Schedule them while you interact with the user so you know what will happen.
Main Developers of Antimalware and Antivirus Programs
There are numerous anti-malware and antivirus software developers, each offering solutions with different features and levels of protection. Below is a list of some of the most prominent and recognized on the market:
NortonLifeLock (formerly Symantec):
Norton Antivirus: One of the best-known antivirus solutions, it offers protection against viruses, spyware, malware and other online threats.
McAfee:
McAfee Total Protection: Offers a full range of security services, including antivirus, antimalware, and identity protection.
Kaspersky Lab:
Kaspersky Internet Security: Known for its high level of malware detection and additional features such as ransomware protection and parental controls.
Bitdefender:
Bitdefender Total Security: Offers a robust combination of antivirus, antimalware, and additional security features such as a firewall and privacy protection.
ESET:
ESET NOD32 Antivirus: Recognized for its effectiveness and low consumption of system resources, offering proactive protection against emerging threats.
Avast:
Avast Free Antivirus: Offers a free version with basic protection features, as well as paid versions with additional features.
AVG Technologies (part of Avast):
AVG Antivirus: Similar to Avast, it offers free and paid versions with different levels of protection.
TrendMicro:
Trend Micro Maximum Security: Offers protection against viruses, malware, and online threats, plus privacy features.
Sophos:
Sophos Home: Known for its focus on business protection, it also offers home solutions with centralized management.
Malwarebytes:
Malwarebytes Premium: Specialized in malware removal, it offers a combination of antivirus and antimalware with real-time protection.
Other notable developers
Panda Security
Panda Dome: Offers a variety of plans with features like real-time protection, VPN, and parental controls.
Webroot:
Webroot Secure Anywhere: Known for its low impact on system performance and fast threat detection.
F-Secure:
F-Secure SAFE: Offers a complete security solution with additional features such as banking and family protection.
Comodo:
Comodo Internet Security: Offers a security suite with an advanced firewall and sandboxing to run suspicious applications in a safe environment.
Choosing an antimalware or antivirus program depends on the user’s specific needs, such as the level of protection desired, the impact on system performance, and any additional features valued. All of the mentioned manufacturers have reputation and experience in the field of computer security, offering a wide range of products that can adapt to different situations and environments.
Why will Computer Security Continue to be Essential?
Cyber security is a critical aspect of the digital age due to the increasing dependence on technology in all facets of life. Here are the key reasons why it has been, is and will continue to be essential:
Historical Importance
Protecting sensitive data: Historically, cybersecurity has been vital to protecting sensitive data, including financial records, personal information, and intellectual property. The early breaches highlighted the need for strong security measures to prevent unauthorized access and data theft.
Preventing early cyber attacks: As computers became interconnected, the potential for cyber attacks increased. Early incidents of viruses and worms spreading through networks demonstrated the need for security measures to prevent widespread outages.
Current Importance
Rise in Cyber Threats: The modern digital landscape faces a multitude of cyber threats, including ransomware, phishing, and advanced persistent threats. These attacks can cause significant financial and reputational damage to individuals and organizations.
Data Privacy Regulations: Current regulations such as GDPR, CCPA and others impose strict data protection rules. Compliance with these laws is essential to avoid legal sanctions and maintain consumer confidence.
Digital transformation: As businesses and services move online, protecting digital assets and transactions becomes crucial. E-commerce, online banking, and digital healthcare are examples where security is paramount to protect sensitive information.
Remote work and cloud computing: The shift towards remote work and the adoption of cloud services has expanded the attack surface. Ensuring secure access to corporate networks and protecting cloud-based data are key concerns.
National security: Cybersecurity is a national security issue, and governments invest heavily in protecting critical infrastructure from cyber attacks that could disrupt essential services and compromise national defense.
Future importance
Technology Advancement: Emerging technologies such as the Internet of Things (IoT), artificial intelligence (AI), and 5G networks introduce new security challenges. Protecting these technologies from exploitation will be crucial.
Greater connectivity: As the world becomes more interconnected, the potential for cyber attacks increases. Ensuring the security of interconnected devices and systems will be essential to avoid cascading failures and widespread outages.
Sophisticated cyberattacks: Cybercriminals and state-sponsored actors continually develop more sophisticated attack methods. Staying ahead of these threats requires continued investment in cybersecurity research and innovation.
Economic impact: The economic impact of cyberattacks can be devastating, affecting global businesses, economies and markets. Strong cybersecurity measures are needed to safeguard economic stability and growth.
Trust and reliability: The future digital economy depends on trust. Consumers and businesses must trust that their data and transactions are secure. Maintaining this trust through effective cybersecurity is essential for the continued growth of digital services.
Cybersecurity is and will continue to be a fundamental aspect of computing due to the changing nature of cyber threats, the increasing dependence on digital systems and the need to protect confidential information. As technology advances and becomes more integrated into everyday life, the importance of robust cybersecurity measures will only grow, ensuring the security, privacy and reliability of digital interactions and infrastructure.
Discover More of Technology Splendor: Explore Our Other Sites
Your Health is your Best Investment
Energy, clarity, and balance are the foundation of every dream. Without health, wealth loses its shine and relationships lose their spark. Discover strategies to strengthen your body, sharpen your mind, and energize your spirit.
Learn How to Protect It →Relationships Give Life Meaning
Health gives you energy. Wealth gives you freedom. But only deep, authentic relationships give life true purpose. Discover the tools to connect, love, and communicate at your best.
Improve your Personal and Business Relationships




